This is what happens when a zone is signed with DNSSec:
- 2 Keypairs are created, named ZSK and KSK.
- The public keys ZSKpub and KSKpub are added to the zone file as DNSKEY RR:s
- All existing entries in the zone files are signed with the ZSKpriv. The signatures are added to the zone files as RRSIG RR:s.
- The added DNSKEY RR:s (ZSKpub and KSKpub) are signed with KSKpriv. The signatures are added to the zone file as RRSIG RR:s.
- A hash of KSKpub is transfered to the parent zone.
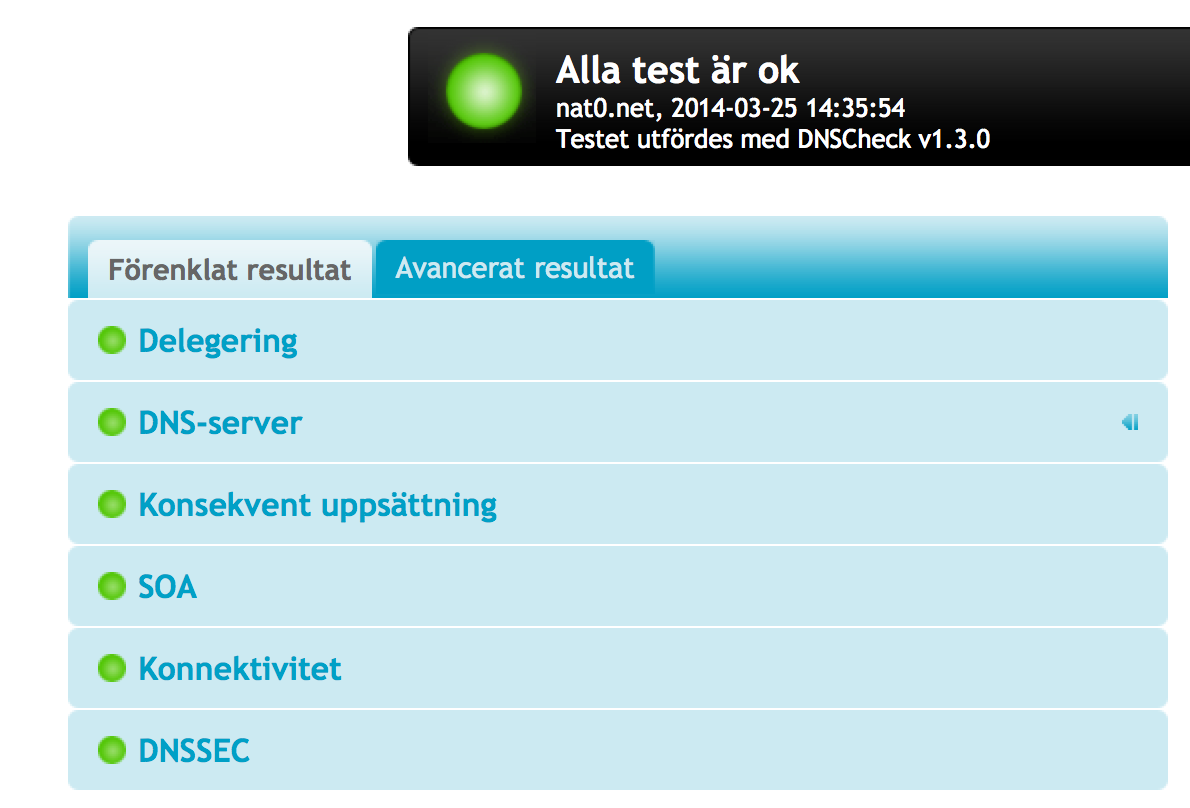
To visualize this we will sign the fictive zone net0.net. This is the unsigned zone file:
$ORIGIN net0.net.
$TTL 300
net0.net. IN SOA ns.nat0.net. abuse.net0.net. (
2014020320
3H ; Refresh after three hours
1H ; Retry after one hour
1W ; Expire after one week
1D ) ; Minimum one day TTL
@ IN 3600 NS ns.net0.net.
ns.net0.net. IN A 89.160.63.216
www IN 3600 A 89.160.63.217
This zone file is heavily simplified. It contains one SOA-record, one NS-record and 2 A-records. So, let´s take a look at what happens when the zone is signed, step by step:
Step 1: 2 Keypairs are created, named ZSK and KSK.
In the configured key directory 4 files are created
Knet0.net.+008+08565.key
Knet0.net.+008+08565.private
Knet0.net.+008+62671.key
Knet0.net.+008+62671.private
Each public key is stored in the files named .key and the content looks something like this:
net0.net. IN DNSKEY 256 3 8 AwEAAdNMI9iWcmphYDJPqAHxuAkduG7uF1UNy/OKrumEXxOZfGydiEDk 7++Yx75UxOWsAvG7MIUXQWthGj59XfRAIfKxcJr+XhpnQdX2rtjPAj8v zJ2ZB/c8iKmYzUQ85pUoHM6TN+/1wfARFfWK1+FmpGPB0pYBDWpLUmDb JAJkREQz
Its private equivalent is named .private and the content of the file looks like this:
Private-key-format: v1.3
Algorithm: 8 (RSASHA256)
Modulus: 00wj2JZyamFgMk+oAfG4CR24bu4XVQ3L84qu6YRfE5l8bJ2IQOTv75jHvlTE5awC8bswhRdBa2EaPn1d9EAh8rFwmv5eGmdB1fau2M8CPy/MnZkH9zyIqZjNRDzmlSgczpM37/XB8BEV9YrX4WakY8HSlgENaktSYNskAmRERDM=
PublicExponent: AQAB
PrivateExponent: K2ftyTWGxZHBaDRy6AtW6hB/7dHdWyydZCduLSxzN5yFMe7eqa4eGBNDnTbex+uhIzV4Dy8q0js9X+7zGRT/o/KPdyxr9y4xBeruKXwHl8nKVdaUsgr21z7zDZ5emlqoPHQ9XryohQyiWgN3qYIU3Cm5de6gl5+Sx5FLaQZjnUE=
Prime1: /+S4XclcoTX2Vnz+ZOGyEdgsz+kofAZfAJazzFVMbc+GBv+7SsjB5PpDwOrxdMSBgq2SYveecjlVwDHiwAOwEw==
Prime2: 02KqZt4b6g6cEOojse02yAEclqTou6mNs+mUk7QCyQvekVGl+mnZqpa/bQ/jMMnXNPDOJTv+KKY1aZLVPUrfYQ==
Exponent1: m5nNziHCdLjmeQL6ggeHizhDT428s2YAYNBCto5rsh5NpnXcwoW++WiAyI9UkadoBTlcWVeu/lAE56Ct/AqCBw==
Exponent2: rxYbRGcWQfDl7dCxzi9IX7MkBdcD+mR/PZTsfsbsQ7A0IrO5QcgpBXYlimVNbdzRB0Wpygd+BhddSFvZihIZIQ==
Coefficient: 2PGzkxeMAtwZi9kgbq8Lb57z8q/flqC92rTU/5iymhOshvilVTX347FS9PZzcN3tsdHG2HCJ8OVAZzlpIoOcuQ==
Step 2. The public keys ZSKpub and KSKpub are added to the zone file as DNSKEY RR:s
The content of the .key-files are added to the zone files with some additional comments:
300 DNSKEY 256 3 8 (
AwEAAdNMI9iWcmphYDJPqAHxuAkduG7uF1UN
y/OKrumEXxOZfGydiEDk7++Yx75UxOWsAvG7
MIUXQWthGj59XfRAIfKxcJr+XhpnQdX2rtjP
Aj8vzJ2ZB/c8iKmYzUQ85pUoHM6TN+/1wfAR
FfWK1+FmpGPB0pYBDWpLUmDbJAJkREQz
) ; ZSK; alg = RSASHA256; key id = 8565
300 DNSKEY 257 3 8 (
AwEAAd8BTQ9YX9b+Ve4bYhOCdtAC9AzVkb4q
eTc0dlXXcv2ALeOb2sdPmMS6DNSjCorFx0zH
ZhUxYVMh1Mtg975wgkUa3mLEWExq7F2+1kPR
h5yDdmNjJnrNypTcXfr6gJ0rZs+nm8BItLeU
hwLZ8YfIK6zZzKWTKa6DgR40GTt0jyjy9wfY
VxIp/bB7HIcMsRrooDG5ZiwGmLPF72oNwN1r
/C+uDCoeaPKghbStjnbcu6I+O5+dcvm9AWA3
cPhwCacSJLGdPxCGeGu5JBDMAjOjXAqeWAcG
yqn3JX85s4pII8hwIqRalFjpgZihfBJw8PME
BWSIO0/h+AQp/e3coWkNy5U=
) ; KSK; alg = RSASHA256; key id = 62671
Step 3: All existing entries in the zone files are signed with the ZSKpriv. The signatures are added to the zone files as RRSIG RR:s.
So, which is which above? Take a look at the number following directly after “DNSKEY”. 256 and 257. The one with the odd number is the KSK. So Key with ID 8065 is our ZSK and 62671 is the KSK. Now, dive into the signed file and have a look. Directly below each original record (SOA, NS, A, A) we have new RRSIG:s:
net0.net. 300 IN SOA ns.nat0.net. abuse.net0.net. (
2014020320 ; serial
10800 ; refresh (3 hours)
3600 ; retry (1 hour)
604800 ; expire (1 week)
86400 ; minimum (1 day)
)
300 RRSIG SOA 8 2 300 (
20140504081944 20140404071944 8565 net0.net.
wLckeJ1hagRD6oKQN49FBJl8Z5OURJWvNvqV
KkjI4F31XUQPRVBxc1uO9yOuyznf7L6UnaPx
ltyCoFZ2hZukm4T/I8CMQ4KIDb5tSj51n8uO
oNyC764ACd3y3BEa/yNrIzjTnrlWQYvDtGP1
ifd1ZN3ytmwK2+mAJzEnwt8meFs= )
3600 NS ns.net0.net.
3600 RRSIG NS 8 2 3600 (
20140504081944 20140404071944 8565 net0.net.
R2KDBRWRq5IJkQVGSR/3L23aGGwJPof7/E7T
LKMkYvpfdIRN6Ftq3armgB7n8i9VYDYf5p+4
k7cBDp6X/Fkk/P0H3jWpqACjRfXR/8mdtZhC
9tfxDTo7GVZE0Nj+ieDiStcDU6MU8YQ5l78B
t5VxrQ7mJjSt0MMZImiUaI4XkfM= )
ns.net0.net. 300 IN A 89.160.63.216
300 RRSIG A 8 3 300 (
20140504081944 20140404071944 8565 net0.net.
D50NhRl2SWmBgGjTrCbUfBG/Vubbn7AWzBT+
ApwWYNG+AvjVOxcGH0Cn/ghABp3VtLFDlEVq
zwhea3A4A/qwRCN2VEKoBg06Z2yGBcg+oC3f
/TcH1mIEcIcaOi/j59o5p0W3TeLV1lOVAdTY
eUfdRHjeBCKb6w6CWgPlpx4x0AM= )
www.net0.net. 3600 IN A 89.160.63.217
3600 RRSIG A 8 3 3600 (
20140504081944 20140404071944 8565 net0.net.
jN80xlpzHnEt0A/H4lX//RC9coqRUPDpe1Lf
6k9SJRmJHg60MbIIlwGmIHjMhWq5VtTZQPIz
HpTbqVIxukJSLLWXTkXykZLPCRE2Xnm3QlTv
hMYPFX1LUqYaGzdbcjRnFFGmq44lOiCSYAre
kKKPWYK9GHbMWE3z4Hxwdu4PC5w= )
Note that each RRSIG has the key-id 8565 included in the record to show which key the signature is created with (the ZSK)).
Step 5: The added DNSKEY RR:s (ZSKpub and KSKpub) are signed with KSKpriv. The signatures are added to the zone file as RRSIG RR:s.
300 RRSIG DNSKEY 8 2 300 (
20140504081944 20140404071944 8565 net0.net.
TSEt2dwC3EU1oUibSnA7wLjUgseTrt3/VpRZ
0wv0pTQ3ikTvYB6q0iHPzZuWDGvLKUf8wqMS
mG6RpbVRu16gFuAjsDDmc3JXdhbBOGj0dRQW
PZVH++NkFJYDe2E8z3T5dcu7EdvN7iPKWlKJ
QyLcEBUibhpRStop32tOrImXjsU= )
300 RRSIG DNSKEY 8 2 300 (
20140504081944 20140404071944 62671 net0.net.
1kg2TK6JVOOiziies2qPRi8mDFPkgM2kiq5c
+tOj1oQoDX+RySxxW9GpKYKdOJJQVAh63nL4
gekJEmGrLEHot68tzhA1UBbIABHSezjlj6z6
NKy/xAzKl6Rc0u1eoNaWEX/kw4dkY4dVqc9i
71N617FLQI0lD1rzF/7KTc94F+49n/9dvzg+
LSvqdIPovwhruIZoU5i/XDwVai/pu2eYEPw9
uGD5KShoCCefJh+UBemHLKtB/PpOhEgRx4hn
ud1ezfyO/KJAyi0dvEDo7UHfbxpW60zEZEC2
tYH9ycLO1snLJvCZ6jz6URUiK8QqP/UicpEp
6yNf6Rlvg7vNmfpZeA== )
Step 5: A hash of KSKpub is transfered to the parent zone.
Instead of sending the entire KSKpub to the parent zone, a hash called DS-set is created. This is smaller than the key itself and the reason for making a smaller DS-set is to save space in the parents zone files. This DS-set is created as a separate file named dsset-<zonename>. in the same directory as the keys. The content of this file is to be sent to the parent. The routine how to do this can differ depending on which registrar your zone is connected to. I have seen situations where the ds-set is sent to the registrar with email but the most common way to do this is to upload the DS-set to the registrar in a web form. This is how the DS-set can look like:
net0.net. IN DS 62671 8 1 99511969D3C5A88E49533476E401A6C9FF0FC5C2
net0.net. IN DS 62671 8 2 6F355545ECDB637BA287C62A075DC28A224AAEDEC6233AA28FC3035C 33557A8D
Disclaimer: This post explains the basic of zone signing. In reality there are a few more things that complicates this even more, like NSEC and double ZSK:s. These topics are to be explained elsewhere. 🙂
So, the chain of trust gives that
- A specific DNS-record is protected with a signature made with ZSK
- The ZSKpub is protected with a signature made with KSK
- The KSKpub is protected with the DS-set stored by the parent.
“Above” that the chain of trust continues all the way up to the root zone “.”.