Short story: With SSH-clients based on OpenSSH 7.0 (like my OSX Mac) I cannot connect with SSH to a Cisco Firewall. To connect anyway I must add the parameter -oKexAlgorithms=+diffie-hellman-group1-sha1 to ssh.
sha1 is deprecated as hash algoritm and should not be used. In some Cisco ASA firewalls running older code you might find that connecting with ssh to the device gives you an error message similar to this:
bash>ssh jimmy@10.192.168.1 Unable to negotiate with 10.192.168.1 port 22: no matching key exchange method found. Their offer: diffie-hellman-group1-sha1 bash>
The quick fix to this is to temporary accept sha1 in your ssh client. In OSX you add the parameter -oKexAlgorithms=+diffie-hellman-group1-sha1 to make the client accept sha1:
bash>ssh -oKexAlgorithms=+diffie-hellman-group1-sha1 jimmy@10.192.168.1 jimmy@10.192.168.1's password: Type help or '?' for a list of available commands. 5506>
The permanent and much better solution is of course to tell the ASA not to use sha1. Unfortunately this is not possible. As a sidenote there is a new feature that comes with version 9.6(1) and 9.1(7).
There must be a ssh cipher configuration command available, if not, upgrade. Like in my box running 9.5(2):
5506(config)# ssh ci? ERROR: % Unrecognized command 5506(config)# ssh ci
After upgrading to 9.6(1) I am able to select ssh cipher parameters both for integrity (hash) and encryption:
5506(config)# ssh cipher integrity ? configure mode commands/options: all Specify all ciphers custom Choose a custom cipher integrity configuration string. fips Specify only FIPS-compliant MACs high Specify only high-strength MACs low Specify low, medium, and high strength MACs medium Specify medium and high strength MACs (default) 5506(config)# ssh cipher encryption ? configure mode commands/options: all Specify all ciphers custom Choose a custom cipher encryption configuration string. fips Specify only FIPS-compliant ciphers high Specify only high-strength ciphers low Specify low, medium, and high strength ciphers medium Specify medium and high strength ciphers (default) 5506(config)#
It is not obvious what these cipher suites means but there is a command “show ssh ciphers” available:
5506(config)# sh ssh ciphers Available SSH Encryption and Integrity Algorithms Encryption Algorithms: all: 3des-cbc aes128-cbc aes192-cbc aes256-cbc aes128-ctr aes192-ctr aes256-ctr low: 3des-cbc aes128-cbc aes192-cbc aes256-cbc aes128-ctr aes192-ctr aes256-ctr medium: 3des-cbc aes128-cbc aes192-cbc aes256-cbc aes128-ctr aes192-ctr aes256-ctr fips: aes128-cbc aes256-cbc high: aes256-cbc aes256-ctr Integrity Algorithms: all: hmac-sha1 hmac-sha1-96 hmac-md5 hmac-md5-96 low: hmac-sha1 hmac-sha1-96 hmac-md5 hmac-md5-96 medium: hmac-sha1 hmac-sha1-96 fips: hmac-sha1 high: hmac-sha1 5506(config)#
But Wooooot??? Only sha1 algorithms available? That was unexpected. Let´s try the highest protocol suite available:
5506(config)# ssh cipher encryption high 5506(config)# ssh cipher integrity high 5506(config)# exit 5506# wr mem
After a restart (just to be sure) I still cannot connect from my Mac:
bash>ssh jimmy@10.192.168.1 Unable to negotiate with 10.192.168.1 port 22: no matching key exchange method found. Their offer: diffie-hellman-group1-sha1 bash>
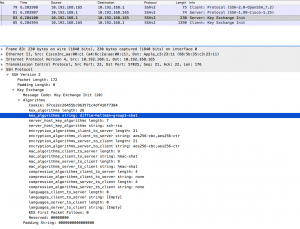
Let´ see how the SSH negotiation looks like. It is Wireshark´O-clock!
This image (click for larger version) shows that the ASA requests DH group 1 with sha1 as the only acceptable protocol for key exchange:
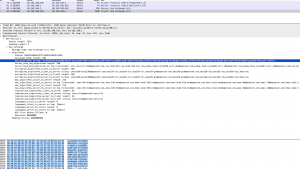
And this image (click for a larger version) shows the reply from the client which is a bit more flexible, offering a lot of different protocols for key exchange, including “diffie-hellman-group-exchange-sha1” which sounds pretty close to “diffie-hellman-group1-sha1” if you ask me.
If someone can tell me the difference between “diffie-hellman-group-exchange-sha1” and “diffie-hellman-group1-sha1”, please write a comment. In the meantime while waiting for Cisco to update the ssh protocol suite in the ASA, use the workaround-parameter stated above.
Update:
Cisco have noticed, waiting for more feedback…
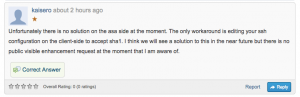
Update2: An answer from Ciscos supportforum:
It seems that this is unresolved from Ciscos side right now…



Hi Jimmy,
Please try ssh key-exchange group dh-group14-sha1,
I tried it on my ASA running 9.6.2 and it worked fine.
Regards
Hakan Nohre
… should add that since I could not SSH to the ASA I just the ASDM CLI interface
to enter the above command.
I can confirm this resolved the issue for me on ASA-5525-X running 9.7(1)
This worked for me. I’m running 9.1(2)
Worked for me with 9.1 as well, thanks!
You star, worked 1st time, saved me a load of pain trying to change my chromebook’s settings…
“ssh key-exchange group dh-group14-sha1”
Just worked for me as well. I don’t fully understand the SSH encryption methods, but no more warnings in putty.
If you’re tired of writing the flag, you can create an SSH config file on your Mac:
vi ~/.ssh/config
And add this line:
KexAlgorithms +diffie-hellman-group1-sha1
I just tried this under asa5505 9.2(4)22 and it worked great!
default was:
ssh key-exchange group dh-group1-sha1
change to:
ssh key-exchange group dh-group14-sha1
Thank so much!!
-here
I see you don’t monetize your blog, don’t waste your traffic, you can earn extra cash every month because you’ve got hi quality content.
If you want to know how to make extra money, search for: Boorfe’s tips best adsense alternative
I have noticed you don’t monetize your website, don’t waste your
traffic, you can earn additional cash every month because you’ve got high quality
content. If you want to know how to make extra $$$, search for: Mertiso’s tips best adsense alternative
For this to work without decreasing the level of security in the SSH client, change the key exchange group in ASA:
# ssh key-exchange group dh-group14-sha1
That is one of the default Kex (key exchange) algorithms for ssh client (at least for OpenSSH). Confirm the default ones in ssh_config and you will see group14 is there
have a nice day
Like!! I blog quite often and I genuinely thank you for your information. The article has truly peaked my interest.