I am currently attending Cisco Live in Berlin. The schedule is stuffed with various nice topics! One of the sessions I just attended was about OpenDNS. I have heard about it and read about it but no more. Since the Cisco acquicision of OpenDNS it is not part of the Cisco Security portfolio.
OpenDNS is a cloud based service that operates between the clients (your and mine computer) and the authoritative DNS servers on internet. By injecting a layer of control into the DNS flow it is possible for OpenDNS to protect us from going to bad sites on internet.
OpenDNS handles more than 80 BILLION dns requests everyday and sees more than 3% of the internet traffic today. With all the insight of internet behaviour they have the power to detect compromized systems, malware C&C-traffic and newly registrated domains used by bad stuff like ranzomware.
It took me less than 5 minutes to sign up for a 14 day trial of OpenDNS, configure basic settings and implement the controls on my laptop as well as iPhone. I have run it for 24h so far and it works great!
Implementing OpenDNS och roaming clients (devices who are not always on the same network) means that some kind of agent/client must be installed. The OpenDNS-client is called Umbrella. This agent authenticates me to the OpenDNS cloud to ensure that the correct policies are implemented (what sites am I allowed to access on internet). Umbrella also makes sure that my DNS traffic is sent to the OpenDNS cloud.
What happens behind the scenes? First, let´s do a DNS lookup on my computer running Umbrella:
jimmy$ dig www.google.com
; <<>> DiG 9.8.3-P1 <<>> www.google.com
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 58382
;; flags: qr rd ra; QUERY: 1, ANSWER: 5, AUTHORITY: 0, ADDITIONAL: 0
;; QUESTION SECTION:
;www.google.com. IN A
;; ANSWER SECTION:
www.google.com. 271 IN A 173.194.113.83
www.google.com. 271 IN A 173.194.113.84
www.google.com. 271 IN A 173.194.113.80
www.google.com. 271 IN A 173.194.113.81
www.google.com. 271 IN A 173.194.113.82
;; Query time: 15 msec
;; SERVER: 127.0.0.1#53(127.0.0.1)
;; WHEN: Wed Feb 17 10:03:21 2016
;; MSG SIZE rcvd: 112
I use 127.0.0.1 as resolver, this was certanly not the case before installing the Umbrella agent.
I have created a custom policy in the OpenDNS cloud that blocks traffic to dn.se, just as a test:
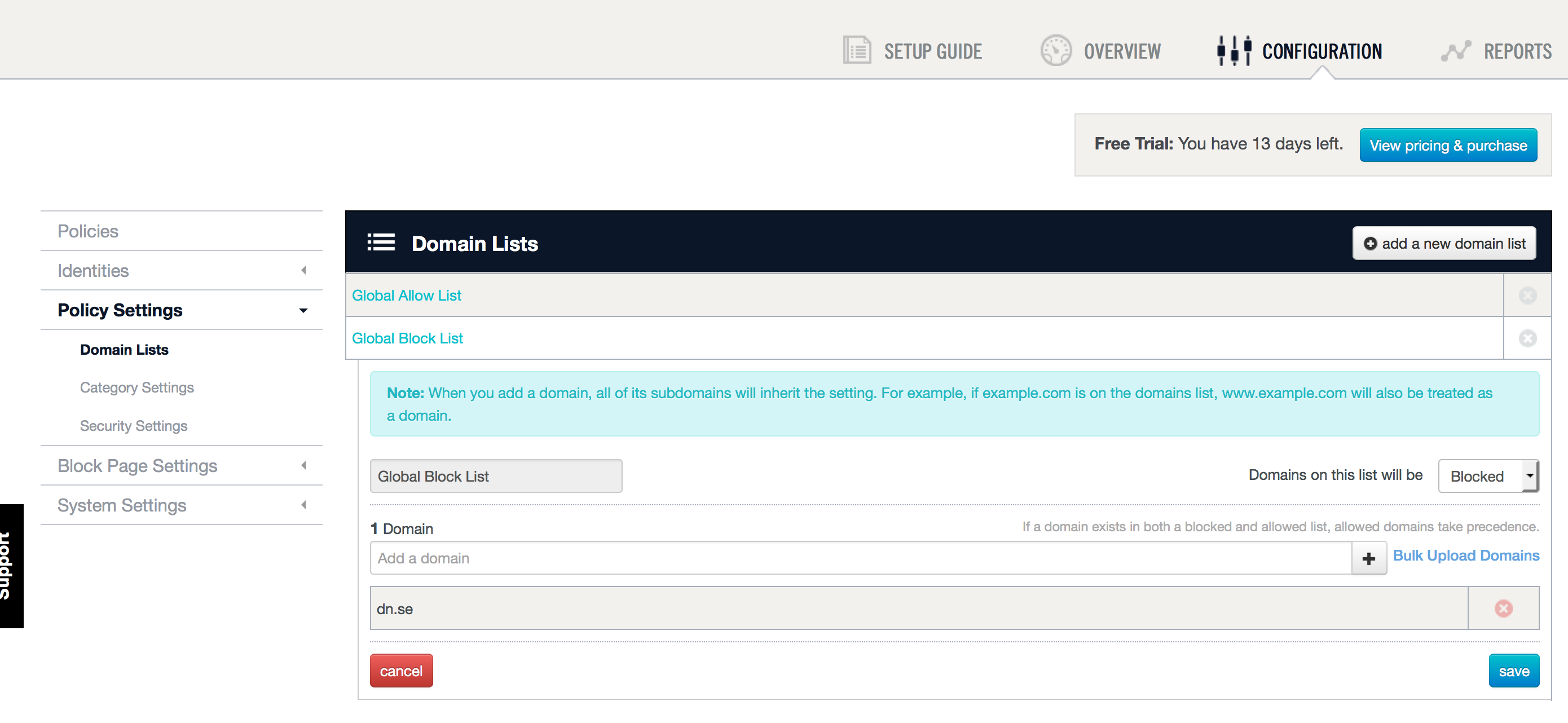
What happens when my computer resolves the entry of www.dn.se?
jimmy$ dig www.dn.se
; <<>> DiG 9.8.3-P1 <<>> www.dn.se
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 39839
;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 0
;; QUESTION SECTION:
;www.dn.se. IN A
;; ANSWER SECTION:
www.dn.se. 0 IN A 146.112.61.104
;; Query time: 13 msec
;; SERVER: 127.0.0.1#53(127.0.0.1)
;; WHEN: Wed Feb 17 10:03:34 2016
;; MSG SIZE rcvd: 43
Looks ok, right? Wait, what is that ip 146.112.61.104?
jimmy$ whois 146.112.61.104
#
# ARIN WHOIS data and services are subject to the Terms of Use
# available at: https://www.arin.net/whois_tou.html
#
# If you see inaccuracies in the results, please report at
# http://www.arin.net/public/whoisinaccuracy/index.xhtml
#
#
# Query terms are ambiguous. The query is assumed to be:
# “n 146.112.61.104”
#
# Use “?” to get help.
#
#
# The following results may also be obtained via:
# http://whois.arin.net/rest/nets;q=146.112.61.104?showDetails=true&showARIN=false&showNonArinTopLevelNet=false&ext=netref2
#
NetRange: 146.112.0.0 – 146.112.255.255
CIDR: 146.112.0.0/16
NetName: RIPE-ERX-146-112-0-0
NetHandle: NET-146-112-0-0-1
Parent: NET146 (NET-146-0-0-0-0)
NetType: Early Registrations, Transferred to RIPE NCC
OriginAS:
Organization: RIPE Network Coordination Centre (RIPE)
RegDate: 2004-02-04
Updated: 2004-02-04
Comment: These addresses have been further assigned to users in
Comment: the RIPE NCC region. Contact information can be found in
Comment: the RIPE database at http://www.ripe.net/whois
Ref: http://whois.arin.net/rest/net/NET-146-112-0-0-1
ResourceLink: https://apps.db.ripe.net/search/query.html
ResourceLink: whois.ripe.net
OrgName: RIPE Network Coordination Centre
OrgId: RIPE
Address: P.O. Box 10096
City: Amsterdam
StateProv:
PostalCode: 1001EB
Country: NL
RegDate:
Updated: 2013-07-29
Ref: http://whois.arin.net/rest/org/RIPE
ReferralServer: whois://whois.ripe.net
ResourceLink: https://apps.db.ripe.net/search/query.html
OrgAbuseHandle: ABUSE3850-ARIN
OrgAbuseName: Abuse Contact
OrgAbusePhone: +31205354444
OrgAbuseEmail: abuse@ripe.net
OrgAbuseRef: http://whois.arin.net/rest/poc/ABUSE3850-ARIN
OrgTechHandle: RNO29-ARIN
OrgTechName: RIPE NCC Operations
OrgTechPhone: +31 20 535 4444
OrgTechEmail: hostmaster@ripe.net
OrgTechRef: http://whois.arin.net/rest/poc/RNO29-ARIN
#
# ARIN WHOIS data and services are subject to the Terms of Use
# available at: https://www.arin.net/whois_tou.html
#
# If you see inaccuracies in the results, please report at
# http://www.arin.net/public/whoisinaccuracy/index.xhtml
#
% This is the RIPE Database query service.
% The objects are in RPSL format.
%
% The RIPE Database is subject to Terms and Conditions.
% See http://www.ripe.net/db/support/db-terms-conditions.pdf
% Note: this output has been filtered.
% To receive output for a database update, use the “-B” flag.
% Information related to ‘146.112.0.0 – 146.112.255.255’
% No abuse contact registered for 146.112.0.0 – 146.112.255.255
inetnum: 146.112.0.0 – 146.112.255.255
netname: OpenDNS-RIPE
descr: OpenDNS
country: EU
admin-c: ODNS36692-RIPE
tech-c: ODNS36692-RIPE
status: LEGACY
mnt-by: OPENDNS-MNT
mnt-routes: OPENDNS-MNT
mnt-domains: OPENDNS-MNT
mnt-by: OPENDNS-MNT
mnt-lower: OPENDNS-MNT
created: 1970-01-01T00:00:00Z
last-modified: 2015-07-29T11:50:40Z
source: RIPE # Filtered
role: OPENDNS NETENG TEAM
address: OpenDNS
address: 675 West Hastings Street, Suite 500
address: Vancouver BC V6B 1N2
address: Canada
phone: +1 415 513 0439
abuse-mailbox: abuse@opendns.com
nic-hdl: ODNS36692-RIPE
mnt-by: OPENDNS-MNT
created: 2014-05-29T13:22:57Z
last-modified: 2015-01-22T18:28:03Z
source: RIPE # Filtered
% This query was served by the RIPE Database Query Service version 1.85.1 (DB-2)
Oh, it seems that the the DNS lookup is intercepted and that the A-records points to OpenDNS instead of the dn.se site. That can be confirmed by trying to browse to the site www.dn.se:
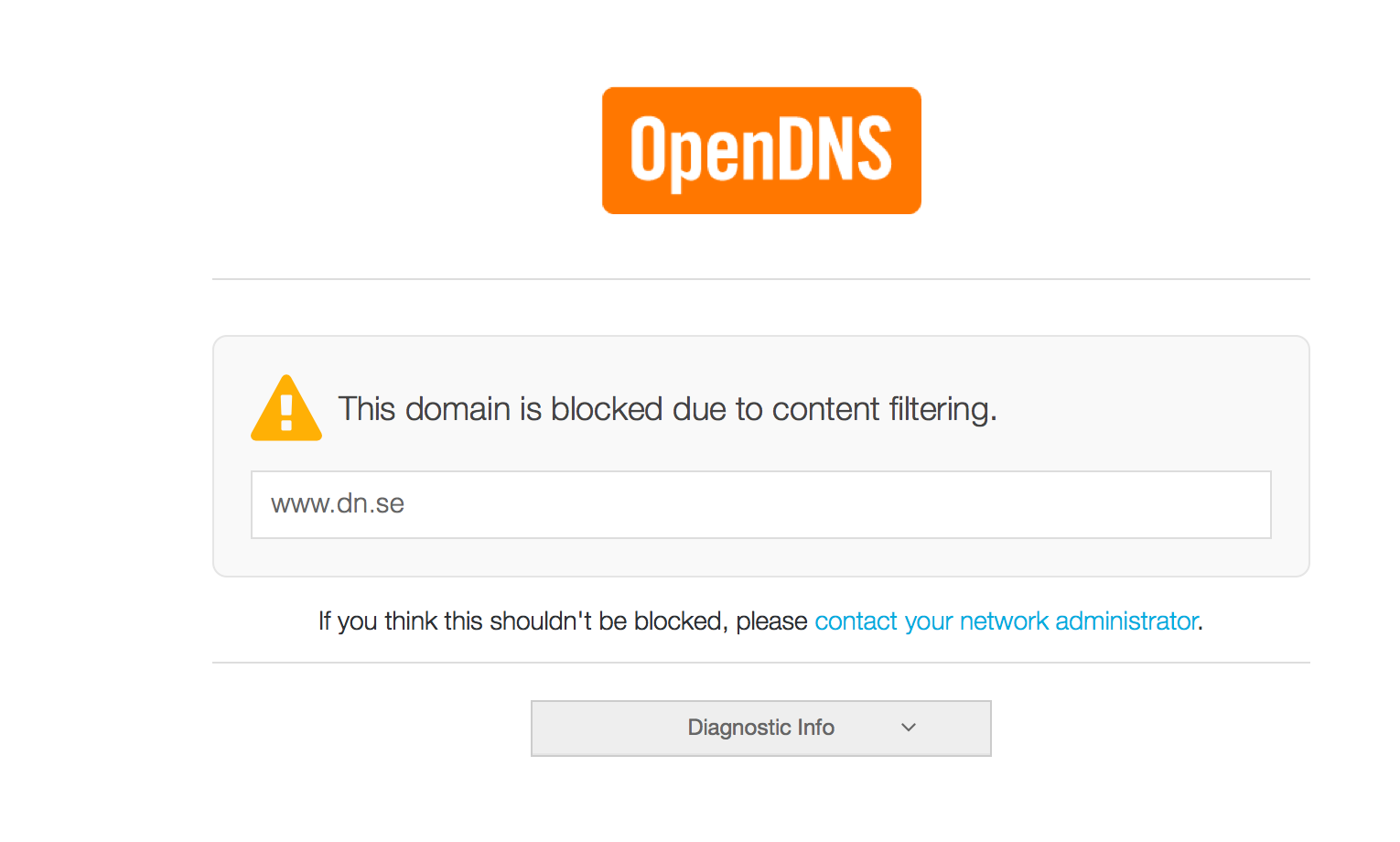 ‘
‘
OpenDNS is not a full web protection system. It does not analyze the traffic, it cannot malware scan web content. But it can drop traffic to dark sides of internet just by using DNS. Not only for web and browser but for ALL Traffic in the client that uses DNS. This is cool!






