This is first in a serie of posts in english dealing with technical configurations and solutions. The reason for this is me studying for CCIE Security certification and along the road I will probably find interresting stuff to share with others in the same situation as I am. (I´ve already found that more good configuration examples can be found at blogs than in technical references as CCO. Another purpose for me posting about stuff like this is that I learn alot when trying to explain and write about it. )
I have been bangning my head a couple of ours now trying to understand the modularity of Cisco ASA MPF. There are Class-maps, policy-maps and service-policies. There are a lot of different types of each of them and different combinations are invalid. Deeper information can be found att CCO.
MPF is built with 3 different types of modules:
- class-maps. Defining what to look for
- policy-maps. What shall we do with it?
- service-policy. where do we do it?
I made up an hypothetical example. Lets say that I want to prevent my users from downloading mp3-files with ftp. This is a good example of when MPF comes handy (yes I know that some users know how to rename files, do encrypted file-transfers or use other protocols than ftp.)
Ok. On my LAN I have this PC with IP 192.168.1.215 which should not be able to GET files whose name contains “.mp3”. Where do I start?
First I create a regexp defining the string to search for:
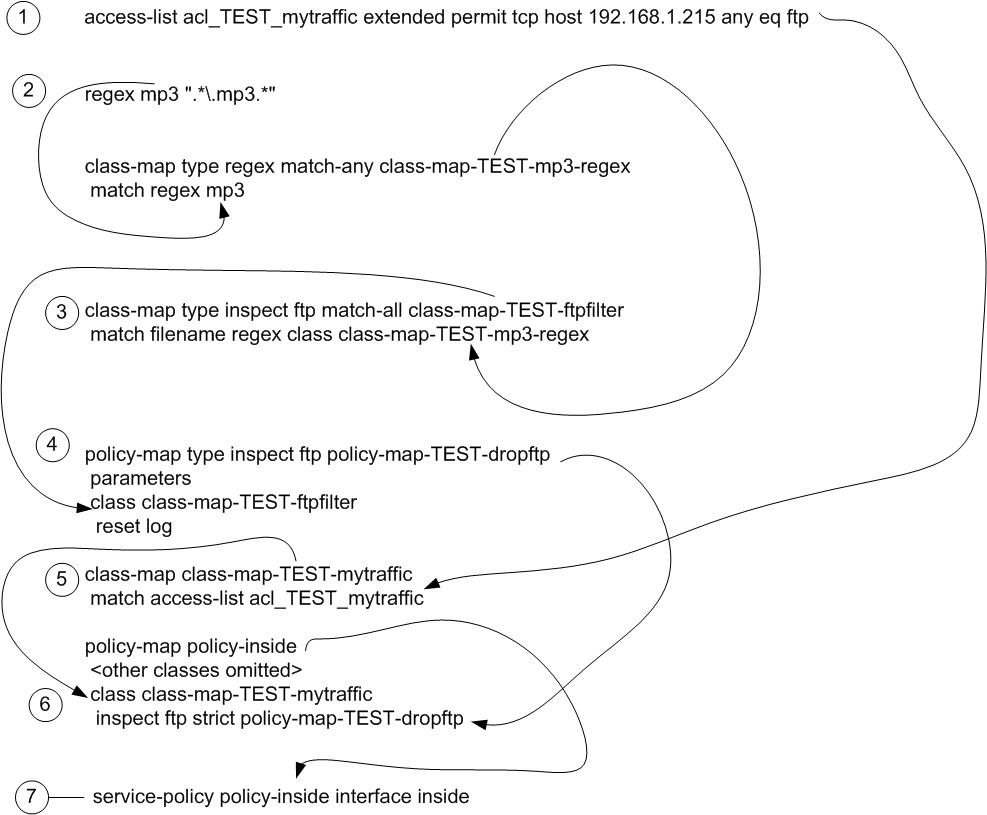
regex mp3 ".*.mp3.*"
Next I create a class-map type regex that uses the regex defined:
class-map type regex match-any class-map-TEST-mp3-regex
match regex mp3
Next thing to do is to create a class-map type inspect which is going to look into the ftp application-data sent and have a look for filenames with the regexp-string matched:
class-map type inspect ftp match-all class-map-TEST-ftpfilter
match filename regex class class-map-TEST-mp3-regex
After that I create a policy-map that defines the action (reset tcp connection and log the event) to be taken when the class-map above is triggered:
policy-map type inspect ftp policy-map-TEST-dropftp
parameters
class class-map-TEST-ftpfilter
reset log
Now I need to define which traffic to look into. Remember the host
-IP above? I create an acl:
access-list acl_TEST_mytraffic extended permit tcp host 192.168.1.215 any eq ftp
Before putting everything together you need to decide where to apply this. It can be done either globally or inbound to a specific interface. The most logical thing to do in this case is to apply it on my inside-interface where my ftp-clients are. If you have already a policy-map bound to that interface you need to reuse that policy-map in the next step. Otherwise, just create a new policy-map.
asa# sh run service-policy
service-policy policy-inside interface inside
asa#
So I reuse this policy and add a new class:
policy-map policy-inside
class class-map-TEST-mytraffic
inspect ftp strict policy-map-TEST-dropftp
Let´s see if it works…
ftp> (connected to FTP-server from my host)
ftp> ls
200 PORT command successful
150 Connecting to port 40538
file.mp3
file.mpt
pub
226 3 matches total
ftp: 25 bytes received in 0,03Seconds 0,96Kbytes/sec.
ftp> get file.mpt
200 PORT command successful
150-Connecting to port 17047
150 3948.3 kbytes to download
226-File successfully transferred
226 4.742 seconds (measured here), 0.81 Mbytes per second
ftp: 4056688 bytes received in 4,79Seconds 847,08Kbytes/sec.
ftp> get file.mp3
200 PORT command successful
Connection closed by remote host.
Finally, a bleeding rocket-science flow-chart with home-made arrows and sugar on top…