This is probably the most perverted form of NAT I have ever done. <flamebait> But, it serves as a proof that with proper NAT there is no need for routing </flamebait>
Scope:
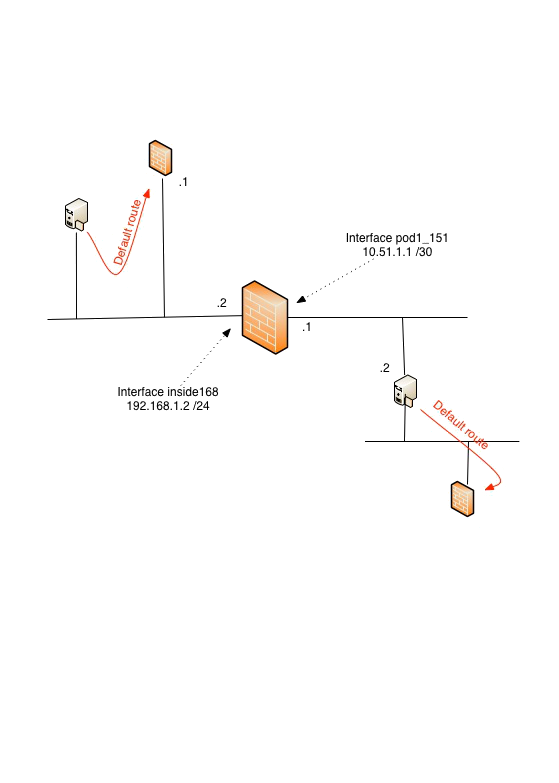
There is a Cisco ASA running code 8.3+ that divides my home network 192.168.1.0/24 from my lab networks. My home devices uses 192.168.1.1 as default gateway and has no other routes configured. Behind the Lab-firewall there is a host with dual NIC:s. The host is connected to my Lab-wirewall via a point2point-network 10.51.1.0/30 and has a default gateway pointing elsewhere.
Goal:
I want the lab-computer to reach my vSphere-server 192.168.1.112:444 and I do also want any computers on my home network to remote control the lab-computer with vnc. I do not want to add extra routes anywhere.
Solution:
object network vCenter
host 192.168.1.112
object network pod1inside
host 10.51.1.2
!
object service RDP
service tcp destination eq 3389
object service RDP_13389
service tcp destination eq 13389
!
object service VNC
service tcp destination eq 5900
object service VNC_5901
service tcp destination eq 5901
object service vSphere
service tcp destination eq 444
!
nat (pod1_151,inside168) source static pod1inside interface destination static interface vCenter service vSphere vSphere
!
nat (inside168,pod1_151) source dynamic any interface destination static interface pod1inside service VNC_5901 VNC
The above configuration makes it possible to:
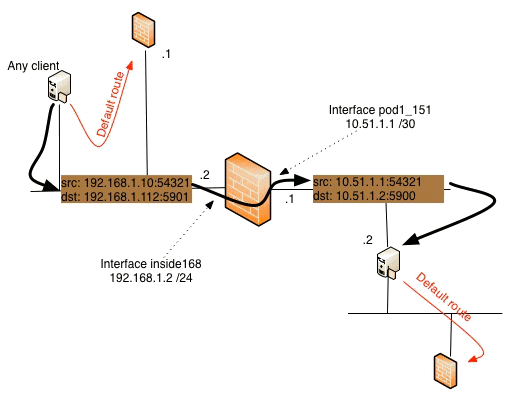
- run the vSphere-client on the lab-computer and connect to 10.51.1.1:444. The source-address of the packet will be translated to the interface-address of inside168 (192.168.1.2) and the destination address will be translated to 192.168.1.112.

- run VNC viewer on any computer on the 192.168.1.0/24-network and connect to 192.168.1.2:5901. The source address of the packet will be translated to the interface address of pod1_151 (10.51.1.1), the destination address will be translated to 10.51.1.2 and the destination port will be translated from 5901 to 5900.



Leave a Reply