I have recently implemented a few Cisco Ironport WSA-solutions. When doing a follow-up after the implementation, the customer usually reacts with “Oh… WSA? We forgot about that. It probably works…”
But what difference does it make? If the customer forgets about their web proxy, what good does it do? Lets have a look at an implementation…
I asked one of our customers for permission to peek into their WSA for the purpose of this blog post. This customer has a few hundred users and is a fairly traditional type of user with mostly office users, each with a personal computer. This customer doesnt limit web browsing, except for filtering out access to known obviously bad web categories like child porn. Except for that, free access to the Web.
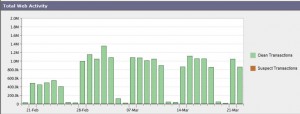
The first thing to look at is an overview of web activity above. The average web traffic an business day is roughly one million is a working day consists of one million web requests. A web page contains several objects (images, scripts) where each object needs to be requested individually. In this implementation the clients generates 1 million transactions (requests) per day, or 20 million transactions per month.
But what is the content of the requested material? If we look at But WHAT users to surf? If you then look at the purity of operations as it starts to get interesting for real!
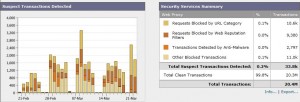
Here you can see that just over 10,000 (10.6K) transactions have been stopped this month because of URL category! That is, such as child porn! There are objects (pages, images, etc.) that the user consciously or unconsciously sought but that the system has already been blocked at the access-trial because the source is known and undesirable.
One can also see that almost 3,000 (2.797) object has been blocked due to malware detection. Remember that the WSA scans all through traffic for known viruses, scripts, or other type of malware. The source category has been approved or unknown the WSA have downloaded content. But when checking the contents, they have discovered something unwanted. This little fella has thus stopped nearly 3,000 viruses in the past month!
Overall, 99.8% of web traffic this month has been “clean”. 0.2% may seem to be disappearing bit, but it is still almost 34 000 (33.8K) potentionella threat that was blocked already at the front door!
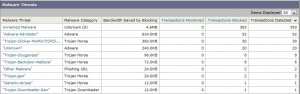
If you want more detailed information about the type of threat blocked, you can obviously get it also:
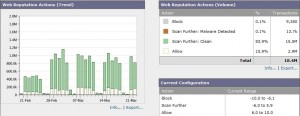
With the help of the dynamic Sender Base system scored all websites on the internet. Based on a number of factors such as known virus outbreak or the credibility of a domain, each site a web reputation score from -10 to +10. WSA is configured to always block the sources with the lowest score and always allow the web site with the highest score. But how does this when in reality?
Here we can see that nearly 10,000 transactions in the last month blocked because of Web reputation.
The conclusion I draw every time I look at this type of reporting is that the WSA is blocking lots of web traffic in the covert, and it’s surprisingly rare that users react to the IT department because they can not browse to a specific site. It may be that the user deliberately tries to make stupid mistakes on the internet, but my experience and absolute conviction is that it almost always is something that happens unconsciously. A link to an email or on facebook that look “nice”, but takes the user to a malware site in some obscure corner of the Internet.
Key figures for this particular device, a typical month “at work”:
- The number of transactions: 20.4 million pieces.
- The number of blocked transactions: 33 800 pcs.
- The number of blocked Malwares / viruses: 2797 pcs, or one every 3 minutes during business hours!
- Dare you not to check the content of your web traffic?



I’ve been pretty happy with what I’ve done with the WSAs too. Not quite as “set and forget” as the email appliances, but not bad. The only times we had to really mess around with them was when some departments wanted quite restricted access – but then specific sites within the blocked categories had to be allowed, and at certain times, by certain staff…All pretty easy to do in the end, just a matter of working out exactly what we were trying to achieve.
I am a little surprised at the level of blocked Malware you’re seeing – last time I went through the reports a couple of years ago I wasn’t seeing all that many. Similar user numbers, maybe a different traffic profile though.
Detailed reporting was a bit of a pig with Sawmill in 2009 – has it gotten any better?
Jeg tænker det samme. Jeg tror, jeg lige ville runde lægen 🙂 Held og lykke og bliv ved med Locobase, sÃ¥ skal det nok hjÃhKpe.l¦. Katja
This sounds all too much like the people I was dealing. I did go to the presentation and left early. I left with a voucher for 4 nights in Orlando, Florida and 3 nights at the beach ( Daytona or Ft. Lauderdale). A $25.00 processing fee was required for the voucher.The address of the presentation center is:Awards Centre6175 Hwy 7, Unit 6Woodbridge, OntarioL4H0P6Behind the reception desk was the name: Premium Buyers Club
I’m having a bit of an issue with the WSA after switching over from Websense. We want to be able to re-categorize some URLs locally that Cisco wont re-categorize globally. This was very simple on Websense, however the custom URL categories in the WSA only allow domains and sub-domains but not something like http://www.website.com/EXAMPLE. We want to keep website.com allowed but add website.com/example to our blacklist, but it doesn’t appear to be possible without Cisco re-categorizing it globally for all WSA customers.
very good
دانلود آهنگ http://www.2.fazmusic38.org/