Today I continued my work to fully understand MPF (Modular Policy Framework) and found a new cool feature in ASA 8.2: TCP State Bypass. By bypassing TCP state machine for certain traffic you can get around problems with asymettricrouting. In my home lab I built this scenario:
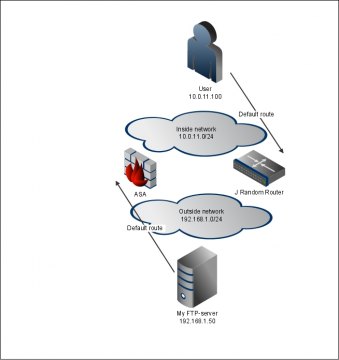
On my inside network I have this client host who wants to access the FTP-server on outside. However, there are multiple links between the networks and the routing seems to be assymmetric. My inside hosts outbound traffic leaves thru the router but the return traffic goes thru the firewall. What happens is that the ASA sees the SYN ACK return packet but havent seen the preceeding SYN-packet. The result is that it blocks the packet:
%ASA-2-106001: Inbound TCP connection denied from 192.168.1.50/21 to 10.0.11.100/59677 flags SYN ACK on interface outside
%ASA-2-106001: Inbound TCP connection denied from 192.168.1.50/21 to 10.0.11.100/59677 flags SYN ACK on interface outside
%ASA-2-106001: Inbound TCP connection denied from 192.168.1.50/21 to 10.0.11.100/59677 flags SYN ACK on interface outside
She solution to this is to configure a policy-map that makes an exception to this state-machine-thing and allows that return-traffic anyway. Lets rock!
First, make sure that the inbound traffic gets thru. Doing state-bypass doesnt mean that acls will be bypassed. Since this is return traffic we need to permit permit with the source-port being 21.
access-list acl_outside extended permit tcp host 192.168.1.50 eq ftp any
access-group acl_outside in interface outside
!
Next, define which traffic to do state-bypassing with. It happens to be the same layout as the acl above. 😉
access-list ACL-STATE-BYPASS extended permit tcp host 192.168.1.50 eq ftp any
Now, create a class-map, give it a fancy name and match the access-list above…
class-map state-bypass
match access-list ACL-STATE-BYPASS
Next, a policy-map which references the class-map above and sets the tcp-state-bypass advanced option.
policy-map POLICY-OUTSIDE
class state-bypass
set connection advanced-options tcp-state-bypass
Finally. Apply it. Since its all about inbound traffic it needs to be applied to outside interface. Remember, if you already hava an service-policy for that interface, addit to that existing policy…
service-policy POLICY-OUTSIDE interface outside
Now, when trying to access my outside FTP-server from my inside client it works. I get this in the ASA-log:
%ASA-6-302303: Built TCP state-bypass connection 47 from outside:192.168.1.50/21 (192.168.1.50/21) to inside:10.0.11.100/37781 (10.0.11.100 /37781)
As you can see I get hitcounts in both access-lists:
fw1# sh access-list acl_outside
access-list acl_outside; 1 elements; name hash: 0xdcd74233
access-list acl_outside line 1 extended permit tcp host 192.168.1.50 eq ftp any (hitcnt=1) 0x6863abc6
fw1# sh access-list ACL-STATE-BYPASS
access-list ACL-STATE-BYPASS; 1 elements; name hash: 0xbe9fc05e
access-list ACL-STATE-BYPASS line 1 extended permit tcp host 192.168.1.50 eq ftp any (hitcnt=1) 0xad18b614
fw1#
Voila! Or “Vålla” as we say in Sweden!


